The Grinch Who Smished Christmas: An Active Campaign Leveraging USPS and the Holiday Spirit
Estimated read time: 4 min
It's the holiday season, bells are ringing, and the Grinch is smishing. Cybercriminals have launched a widespread smishing campaign leveraging the holiday spirit and the United States Postal Service (USPS).
What is smishing?
Smishing, short for "SMS phishing," is a scam where attackers use text messages to impersonate banks, government agencies, or online retailers, to trick victims into sharing sensitive information. Smishing leverages trust, urgency, and deception to manipulate victims, but via text message. For a deeper dive into smishing, check out Smishing: Theft of Information via Text Message.
This article explores an active (as of the date of this article) smishing campaign targeting the rush of online shopping spurred by the holiday season. Attackers know we're online spending and impatiently waiting for those packages in the mail. They're leveraging the identity of the USPS to build trust and creating urgency with fake notifications about delivery failures.
The USPS Smishing Campaign
⚠️ Warning ⚠️ It goes without saying, but do not visit any of the URLs you see listed in this blog post. They are malicious and you could be compromised.
Today I received this message claiming to be the United States Postal Service from an unrecognized sender:

The URL is cleverly crafted using usps. as a subdomain to their malicious domains that starts with com-. This common tactic causes it to appear as though the link leads to https://usps.com, the official USPS website. The message creates a sense of urgency by claiming that the package cannot be delivered. While this message is obviously fake to many online shoppers, these indicators of trust are enough for some to click the link.
Following the Yellow Brick Road
I decided this might not be Santa's elves, so I donned my detective hat and rolled up my sleeves. I first visited https://urlscan.io where I dropped the link in the scanner. The screen lit up like a 🎄Christmas🎄tree🎄 (pun intended 🤭😁). What you're about to see is not for the faint of heart:
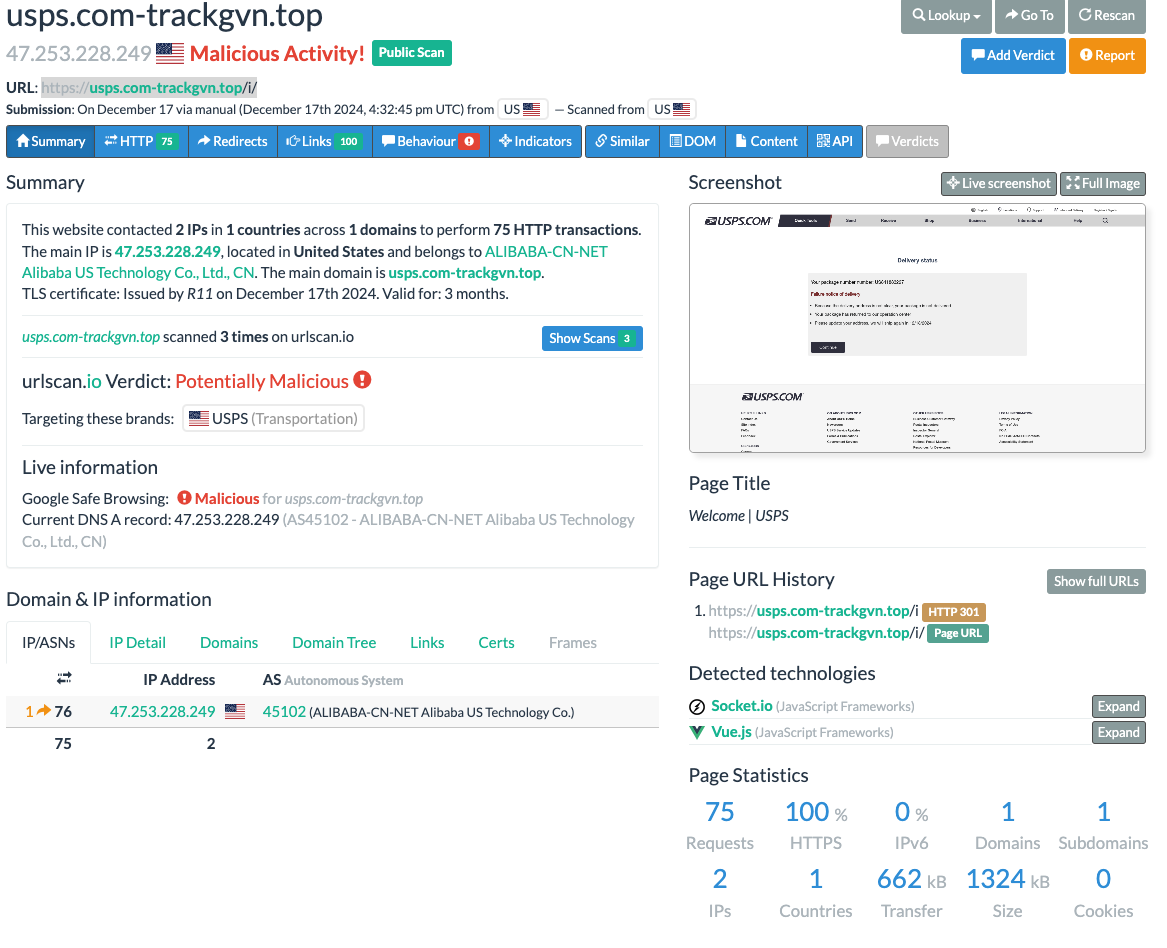
This scan reveals that the link is "potentially malicious". I beg to differ, we KNOW it's malicious... but how?
- The message came from a number in the Philippines, not the United States.
- The server is hosted on Alibaba Cloud, but you'd be hard-pressed to find any legitimate USPS services hosted on Chinese servers, even if the Alibaba labels them "US".
- The TLS certificate was issued December 17th, 2024, the day I received the message. This may not always be suspicious, but it's a bright red flag in this case.
- Google Safe Browsing flagged the site as malicious.
- The URL says USPS, but it's obviously a copycat domain crafted to appear official.
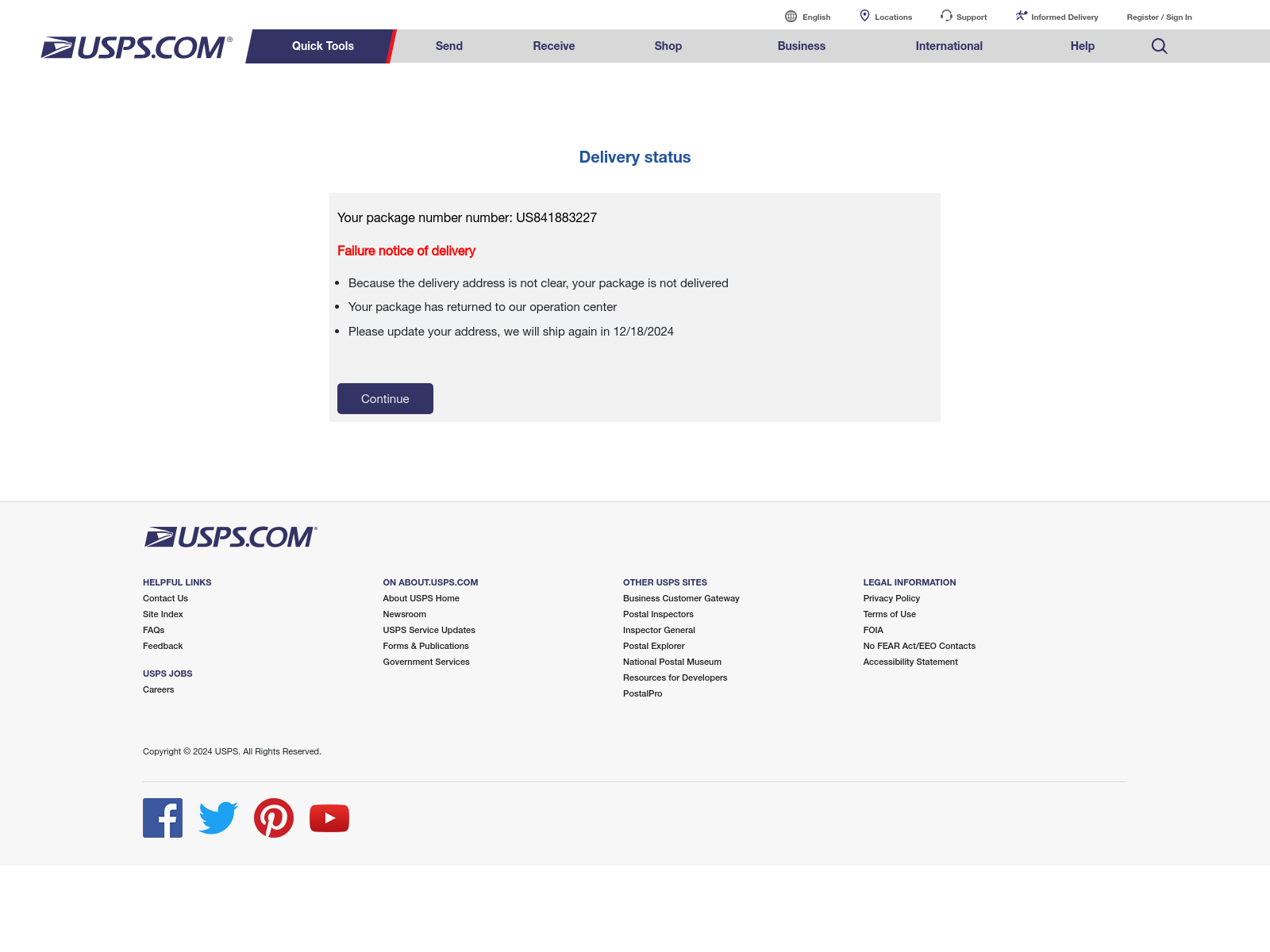
- The screenshot of the page provided by urlscan.io shows a USPS copycat, but we've already established that this certainly isn't the official USPS site.
Here's what it looks like:
What's the Impact of a Campaign Like This?
Some light research shows that this campaign is relatively large. I searched https://urlscan.io/search/# for usps.com-* and found a large number of results. It appears that this threat actor is enumerating com-trackxxxx.top/* domains where xxxx and /* are random character sets. Here's a look at those search results:
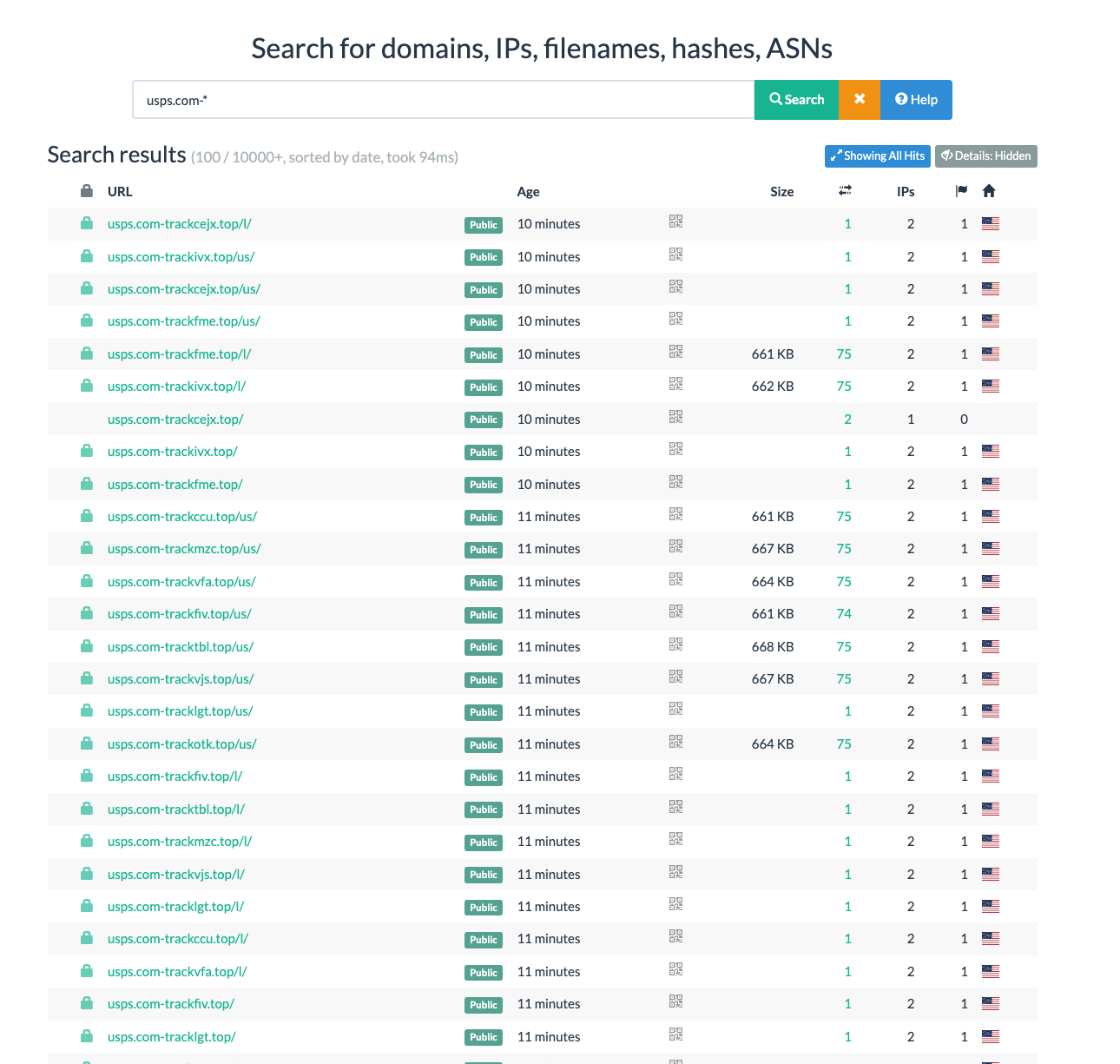
So while this campaign is obviously fraudulent, it's also widespread and likely successful in at least some small percentage of cases.
Additionally, the text message instructs users to exit the message and return or open the link in Safari. This is because iPhones have a security setting that prevents URLs from hyperlinking on the first open from unknown contacts. Android phones may have a similar setting, but this combined with the senders use of iMessage leads me to believe they're targeting iPhone's.
This led me to review the urlscan in more detail. Navigating to the network tab and filtering for scripts led to the discovery of 11 obfuscated scripts written in JavaScript. These scripts may be intended to collect information from the user's device or install some form of malware. I haven't done any further investigation on the code samples so I cannot confirm this is the case. Here's what I found:
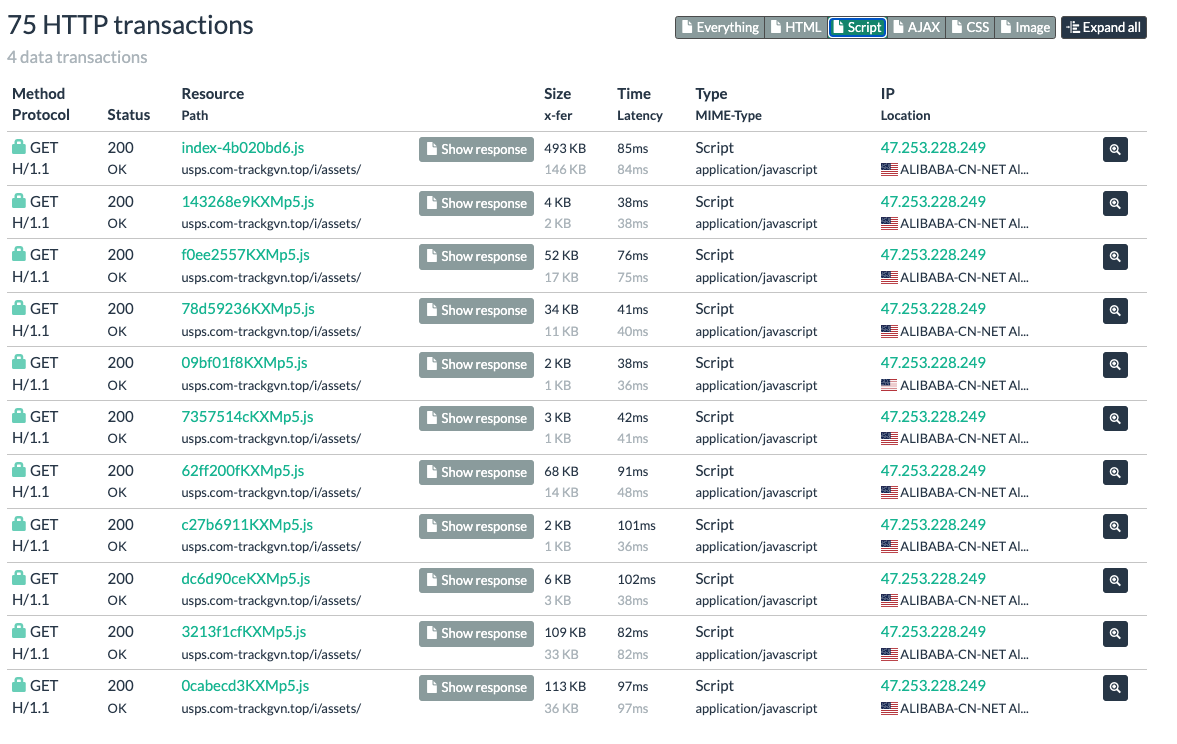
A little dash of obfuscated code for good measure:
One thing is clear: this isn't just a holiday nuisance. Smishing campaigns like this have real, measurable consequences. What seems like an isolated text message can quickly snowball into:
- Compromised Accounts: A single click on a malicious link can result in stolen credentials, giving attackers access to sensitive systems.
- Financial Fraud: Smishing campaigns trick people into approving unauthorized transactions or sharing confidential financial information.
- Pain, Suffering, Lost Time: The Grinch who smished Christmas might strike now, but you'll be dealing with the aftermath long after the holiday season ends.
